
It has been Patch Tuesday again and Microsoft has released a new set of important Exchange Security Updates, released together with this month’s Microsoft Updates.
It is important to keep Your Exchange Servers up-to-date, see the blog post from the Exchange Team on this: Protect Your Exchange Servers
The latest Exchange Security Updates address vulnerabilities found in the following Exchange Servers:
- Exchange 2016 CU23
- Exchange 2019 CU12 and CU13
For more about the vulnerabilities, see the CVEs:
- CVE-2023-21709 – Microsoft Exchange Server Elevation of Privilege Vulnerability
- CVE-2023-35368 – Microsoft Exchange Remote Code Execution Vulnerability
- CVE-2023-35388 – Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2023-38181 – Microsoft Exchange Server Spoofing Vulnerability
- CVE-2023-38182 – Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2023-38185 – Microsoft Exchange Server Remote Code Execution Vulnerability
Be aware of the known issues with this release
- Exchange Server 2019 and 2016 August 2023 security update installation fails on non-English operatin…
- Customers impacted by the upcoming Microsoft 365 AES256-CBC encryption change need to perform a manual action to enable the new encryption algorithm after August 2023 SU is installed. Please see this KB article. We will remove the requirement for manual action in a future update.
Issues resolved in this release
The Security Update is available for the specific Cumulative Update level (CU) your Exchange is running, if you are not up-to-date, with the latest CU, you might have to update the CU before applying the Security Update.
The update path is the following:
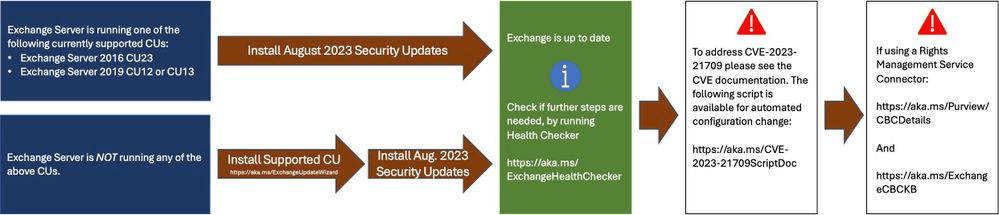
If you are uncertain, about what Exchange Server updates are needed and what current build, your Exchange Servers are running, you can use the Exchange Server Health Checker script to inventory your servers.
If you only have an Exchange Hybrid running, you will still need to update your Exchange environment. You do not need to re-run the Hybrid Configuration Wizard (HCW) after applying updates.
Read the full process on this, on the Exchange Team blog:
Use the Exchange Update Wizard, if any doubt about the upgrade process:
If you manually install the March 2023 Exchange Security Updates, they can be downloaded here:
Download the Security Update that is specific to the CU, your Exchange Server is running.
Remember if you install them manually, the install (.msp file) needs to be run from an elevated command prompt.
More details from the original Exchange Team blog post:
It is recommended to update your Exchange Servers as soon as possible. Remember to test the updates if possible in your test environment, before implementing them in production.
/Happy Patching! 🙂